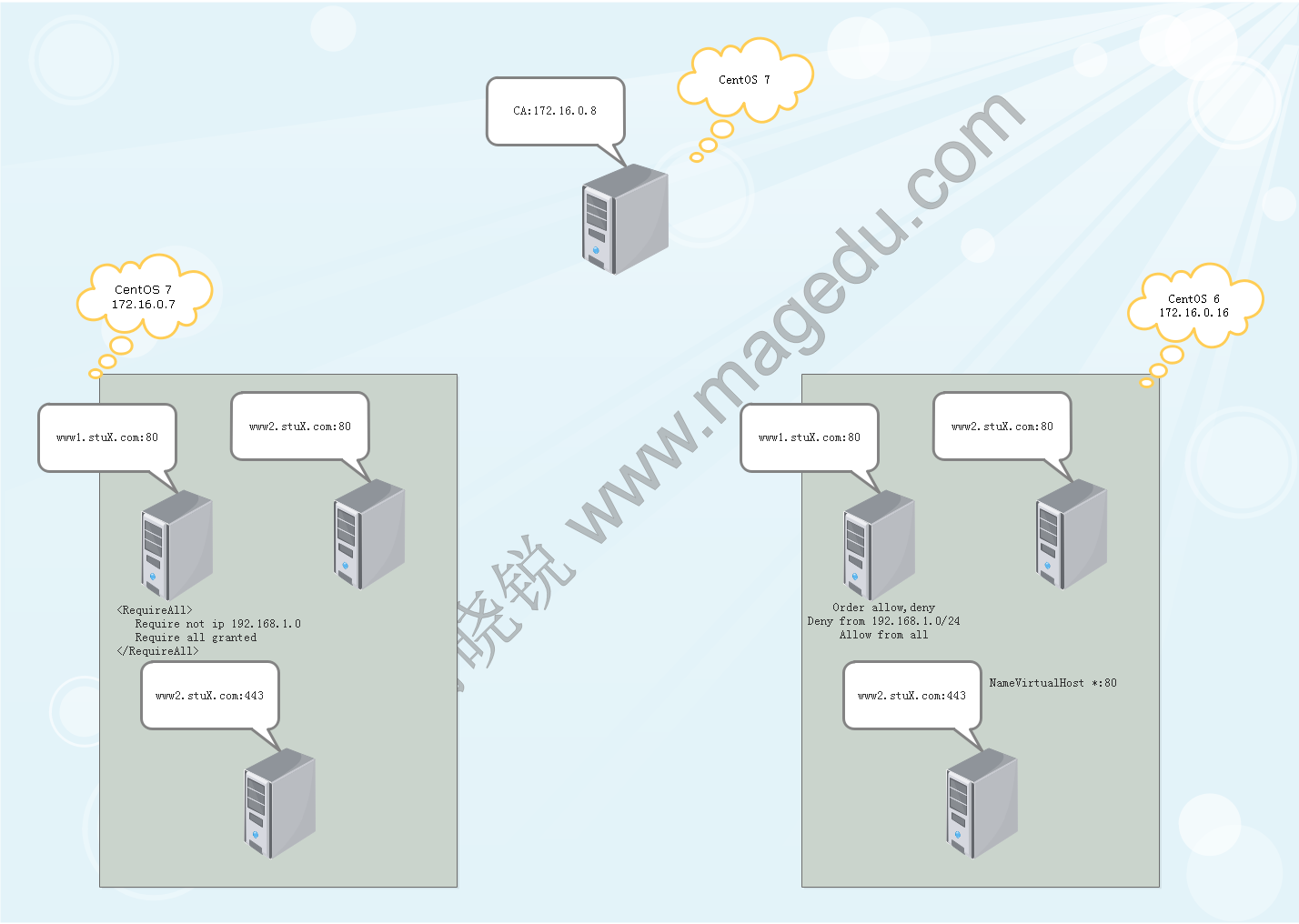
1、建立httpd服务,要求:
(1) 提供两个基于名称的虚拟主机:
www1.stuX.com,页面文件目录为/web/vhosts/www1;错误日志为/var/log/httpd/www1/error_log,访问日志为/var/log/httpd/www1/access_log;
www2.stuX.com,页面文件目录为/web/vhosts/www2;错误日志为/var/log/httpd/www2/error_log,访问日志为/var/log/httpd/www2/access_log;
(2) 通过www1.stuX.com/server-status输出其状态信息,且要求只允许提供账号的用户访问;
(3) www1不允许192.168.1.0/24网络中的主机访问;2、为上面的第2个虚拟主机提供https服务,使得用户可以通过https安全的访问此web站点;
(1) 要求使用证书认证,证书中要求使用国家(CN),州(Beijing),城市(Beijing),组织为(MageEdu);
(2) 设置部门为Ops, 主机名为www2.stuX.com;
1、(1)CentOS 6主机
# vim /etc/conf.d/virtualhost.conf
NameVirtualHost *:80
<VirtualHost *:80>
ServerName www1.stuX.com
DocumentRoot “/web/vhosts/www1”
CustomLog logs/www1/access_log combined
ErrorLog logs/www1/error_log
</VirtualHost><VirtualHost *:80>
ServerName www2.stuX.com
DocumentRoot “/web/vhosts/www2”
CustomLog logs/www2/access_log combined
ErrorLog logs/www2/error_log
</VirtualHost># mkdir -pv /web/vhosts/www{1,2}
# mkdir /var/log/httpd/www{1,2}
# httpd -t
# service httpd restart给出测试页面:
# echo “www1.stuX.com” > /web/vhosts/www1/index.html
# echo “www2.stuX.com” > /web/vhosts/www2/index.html在hosts文件中添加解析条目:
# vim /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
172.16.0.16 www1.stuX.com www1
172.16.0.16 www2.stuX.com www2测试访问:
# curl http://www1
www1.stuX.com
# curl http://www2
www1.stuX.com
(2)输出状态页面
# vim /etc/conf.d/virtualhost.conf
NameVirtualHost *:80
<VirtualHost *:80>
ServerName www1.stuX.com
DocumentRoot “/web/vhosts/www1”
CustomLog logs/www1/access_log combined
ErrorLog logs/www1/error_log
<Location /server-status>
SetHandler server-status
AuthType basic
AuthName “VIP”
AuthUserFile “conf.d/.htpasswd”
Require valid-user
</Location>
</VirtualHost><VirtualHost *:80>
ServerName www2.stuX.com
DocumentRoot “/web/vhosts/www2”
CustomLog logs/www2/access_log combined
ErrorLog logs/www2/error_log
</VirtualHost>提供账号
# htpasswd -c -b -s /etc/conf.d/.htpasswd tom magedu
# htpasswd -b -s /etc/conf.d/.htpasswd jack magedu
# htpasswd -b -s /etc/conf.d/.htpasswd obama magedu
# cat /etc/conf.d/.htpasswd
tom:{SHA}AAXfhrY/nwrcGaafjs69saZnPt4=
jack:{SHA}AAXfhrY/nwrcGaafjs69saZnPt4=
obama:{SHA}AAXfhrY/nwrcGaafjs69saZnPt4=# httpd -t
# service httpd restart
测试访问
# curl –basic -u tom:magedu http://www1/server-status
# curl –basic -u jack:magedu http://www1/server-status
(3)www1不允许192.168.1.0/24网络访问
# vim /etc/conf.d/virtualhost.conf
NameVirtualHost *:80
<VirtualHost *:80>
ServerName www1.stuX.com
DocumentRoot “/web/vhosts/www1”
CustomLog logs/www1/access_log combined
ErrorLog logs/www1/error_log
<Location /server-status>
SetHandler server-status
AuthType basic
AuthName “VIP”
AuthUserFile “conf.d/.htpasswd”
Require valid-user
</Location>
<Directory “/web/vhosts/www1”>
Options None
AllowOverride None
Order allow,deny
Deny from 192.168.1.0/24
Allow from all
</Directory>
</VirtualHost><VirtualHost *:80>
ServerName www2.stuX.com
DocumentRoot “/web/vhosts/www2”
CustomLog logs/www2/access_log combined
ErrorLog logs/www2/error_log
</VirtualHost># httpd -t
# service httpd restart
2、(1)CentOS 6主机
# httpd -t -D DUMP_VHOSTS
*:80 is a NameVirtualHost
default server www1.stuX.com (/etc/httpd/conf.d/virtualhost.conf:2)
port 80 namevhost www1.stuX.com (/etc/httpd/conf.d/virtualhost.conf:2)
port 80 namevhost www2.stuX.com (/etc/httpd/conf.d/virtualhost.conf:23)为第二个提供ssl,即是SSL的主机名同www2.stuX.com,且相同的DocumentRoot;
(2)在CA主机生成私钥,自签证书
# (umask 077; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 7300Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Beijing
Locality Name (eg, city) [Default City]:Beijing
Organization Name (eg, company) [Default Company Ltd]:MageEdu
Organizational Unit Name (eg, section) []:Ops
Common Name (eg, your name or your server’s hostname) []:ca.stuX.com
Email Address []:# touch /etc/pki/CA/index.txt
# echo 01 > /etc/pki/CA/serial
(3)在用到证书的主机生成私钥,生成证书签署请求
# mkdir /etc/httpd/ssl
# (umask 077; openssl genrsa -out /etc/httpd/ssl/httpd.key 2048)
# openssl req -new -key /etc/httpd/ssl/httpd.key -out /etc/httpd/ssl/httpd.csr -days 365Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Beijing
Locality Name (eg, city) [Default City]:Beijing
Organization Name (eg, company) [Default Company Ltd]:MageEdu
Organizational Unit Name (eg, section) []:Ops
Common Name (eg, your name or your server’s hostname) []:www2.stuX.com
Email Address []:Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
(4)将请求可靠的发送到CA
# scp /etc/httpd/ssl/httpd.csr root@172.16.0.8:/tmp
(5)CA签署请求
# openssl ca -in /tmp/httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365
(6)下载证书
# scp root@172.16.0.8:/etc/pki/CA/certs/httpd.crt /etc/httpd/ssl
(7)安装mod_ssl模块
# yum install mod_ssl
(8)配置ssl
# /etc/httpd/conf.d/ssl.conf
DocumentRoot “/web/vhosts/www2”
ServerName www2.stuX.com:443
SSLCertificateFile /etc/httpd/ssl/httpd.crt
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key
# httpd -t
# service httpd restart
# ss -tnl
(9)CA主机上测试连接
# openssl s_client -connect 172.16.0.16:443 -CAfile cacert.pem
Verify return code: 0 (ok)
—
GET /index.html HTTP/1.1
Host: 172.16.0.16HTTP/1.1 200 OK
Date: Tue, 28 Nov 2017 15:35:40 GMT
Server: Apache/2.2.15 (CentOS)
Last-Modified: Tue, 28 Nov 2017 14:56:55 GMT
ETag: “e0006-e-55f0c3ae502c7”
Accept-Ranges: bytes
Content-Length: 14
Connection: close
Content-Type: text/html; charset=UTF-8www2.stuX.com
closed
2、(1)CentOS 7主机
# yum -y install httpd httpd-tools
# vim /etc/httpd/conf.d/www1.conf
<VirtualHost 172.16.0.7:80>
ServerName www1.stuX.com
DocumentRoot “/web/vhosts/www1”
<Directory “/web/vhosts/www1”>
Options None
AllowOverride None
Require all granted
</Directory>
CustomLog logs/www1/access_log combined
ErrorLog logs/www1/error_log
</VirtualHost># cp /etc/httpd/conf.d/www1.conf /etc/httpd/conf.d/www2.conf
# sed -i ‘s,www1,www2,g’ www2.conf
# mkdir -pv /web/vhosts/www{1,2}
# mkdir -v /var/log/httpd/www{1,2}
# httpd -t
# systemctl start httpd.service# echo “<h1>www1.stuX.com</h1>” > /web/vhosts/www1/index.html
# echo “<h1>www2.stuX.com</h1>” > /web/vhosts/www2/index.html# vim /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
172.16.0.7 www1.stuX.com www1
172.16.0.7 www2.stuX.com www2# curl http://www1.stuX.com
<h1>www1.stuX.com</h1>
# curl http://www2.stuX.com
<h1>www2.stuX.com</h1>(2)为www1提供状态页面
# vim /etc/httpd/conf.d/www1.conf
<VirtualHost 172.16.0.7:80>
ServerName www1.stuX.com
DocumentRoot “/web/vhosts/www1”
<Directory “/web/vhosts/www1”>
Options None
AllowOverride None
Require all granted
</Directory>
CustomLog logs/www1/access_log combined
ErrorLog logs/www1/error_log
<Location /server-status>
SetHandler server-status
AuthType basic
AuthName “VIP”
AuthUserFile “conf.d/.htpasswd”
Require valid-user
</Location>
</VirtualHost># htpasswd -c -b -m /etc/httpd/conf.d/.htpasswd tom magedu
# htpasswd -b -s /etc/httpd/conf.d/.htpasswd jack magedu
# htpasswd -b -s /etc/httpd/conf.d/.htpasswd obama magedu# cat /etc/httpd/conf.d/.htpasswd
tom:$apr1$uehD6ESz$6HCTYDjx60M.SNLEHNQZO0
jack:{SHA}AAXfhrY/nwrcGaafjs69saZnPt4=
obama:{SHA}AAXfhrY/nwrcGaafjs69saZnPt4=# httpd -t
# systemctl restart httpd.service
#
# curl –basic -u tom:magedu http://www1.stuX.com/index.html
(3)不允许192.168.0.1/24网络内的主机访问www1
# vim /etc/httpd/conf.d/www1.conf
<VirtualHost 172.16.0.7:80>
ServerName www1.stuX.com
DocumentRoot “/web/vhosts/www1”
<Directory “/web/vhosts/www1”>
Options None
AllowOverride None
<RequireAll>
Require not ip 192.168.0.1/24
Require all granted
</RequireAll>
</Directory>
CustomLog logs/www1/access_log combined
ErrorLog logs/www1/error_log
<Location /server-status>
SetHandler server-status
AuthType basic
AuthName “VIP”
AuthUserFile “conf.d/.htpasswd”
Require valid-user
</Location>
</VirtualHost>
# httpd -t
# systemctl restart httpd.service
CentOS 7
2、
在已建CA上,申请证书;
(1)生成私钥及请求
# mkdir -v /etc/httpd/ssl/
# (umask 077; openssl genrsa -out /etc/httpd/ssl/httpd.key 2048)
# openssl req -new -key /etc/httpd/ssl/httpd.key -out /etc/httpd/ssl/httpd.csr -days 365Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Beijing
Locality Name (eg, city) [Default City]:Beijing
Organization Name (eg, company) [Default Company Ltd]:MageEdu
Organizational Unit Name (eg, section) []:Ops
Common Name (eg, your name or your server’s hostname) []:www2.stuX.com
Email Address []:Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:# scp /etc/httpd/ssl/httpd.csr root@172.16.0.8:/tmp/
(2)CA签署请求
吊销上一个主机的证书
# openssl x509 -in /etc/pki/CA/certs/httpd.crt -noout -serial -subject
# openssl ca -revoke /etc/pki/CA/newcerts/01.pem
# echo 01 > crlnumber
# openssl ca -gencrl -out /etc/pki/CA/crl/httpd.crl
# openssl crl -in /etc/pki/CA/crl/httpd.crl -noout -text# openssl ca -in /tmp/httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365
# scp root@172.16.0.8:/etc/pki/CA/certs/httpd.crt /etc/httpd/ssl
(3)安装配置SSL
# yum -y install mod_ssl
# httpd -t -D DUMP_VHOSTS
172.16.0.7:80 is a NameVirtualHost
default server www1.stuX.com (/etc/httpd/conf.d/www1.conf:1)
port 80 namevhost www1.stuX.com (/etc/httpd/conf.d/www1.conf:1)
port 80 namevhost www2.stuX.com (/etc/httpd/conf.d/www2.conf:1)
*:443 is a NameVirtualHost
default server localhost.localdomain (/etc/httpd/conf.d/ssl.conf:56)
port 443 namevhost localhost.localdomain (/etc/httpd/conf.d/ssl.conf:56)
port 443 namevhost localhost.localdomain (/etc/httpd/conf.d/ssl.conf:56)# vim /etc/httpd/conf.d/ssl.conf
DocumentRoot “/web/vhosts/www2”
ServerName www2.stuX.com:443
SSLCertificateFile /etc/httpd/ssl/httpd.crt
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key# httpd -t
# systemctl restart httpd.service
(4)在CA主机访问
# openssl s_client -connect 172.16.0.7:443 -CAfile /etc/pki/CA/cacert.pem
Start Time: 1512215742
Timeout : 300 (sec)
Verify return code: 0 (ok)
—
GET /index.html HTTP/1.1
Host: 172.16.0.7HTTP/1.1 403 Forbidden
Date: Sat, 02 Dec 2017 11:50:46 GMT
Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.1e-fips
Content-Length: 212
Content-Type: text/html; charset=iso-8859-1<!DOCTYPE HTML PUBLIC “-//IETF//DTD HTML 2.0//EN”>
<html><head>
<title>403 Forbidden</title>
</head><body>
<h1>Forbidden</h1>
<p>You don’t have permission to access /index.html
on this server.</p>
</body></html>
(5)配置SSL授权目录
# vim /etc/httpd/conf.d/ssl.conf
<Directory “/web/vhosts/www2”>
Options None
AllowOverride None
Require all granted
</Directory>
(6)在CA主机访问
# openssl s_client -connect 172.16.0.7:443 -CAfile /etc/pki/CA/cacert.pem
# httpd -t
# systemctl restart httpd.serviceStart Time: 1512215937
Timeout : 300 (sec)
Verify return code: 0 (ok)
—
GET /index.html HTTP/1.1
Host: 172.16.0.7HTTP/1.1 200 OK
Date: Sat, 02 Dec 2017 11:53:47 GMT
Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.1e-fips
Last-Modified: Sat, 02 Dec 2017 11:23:09 GMT
ETag: “17-55f59b5bd19a3”
Accept-Ranges: bytes
Content-Length: 23
Content-Type: text/html; charset=UTF-8<h1>www2.stuX.com</h1>
本文来自投稿,不代表Linux运维部落立场,如若转载,请注明出处:http://www.178linux.com/89222